White Box Cybersecurity, Because Of Black Box AI
Check out the picture at the head of this post. It's from a deck made public by Mary Meeker at Bond Capital in May 2025, and it shows the frequency of searches using ChatGPT (a good initial proxy for "generic AI") v. Google searches per year, starting from initial launch.
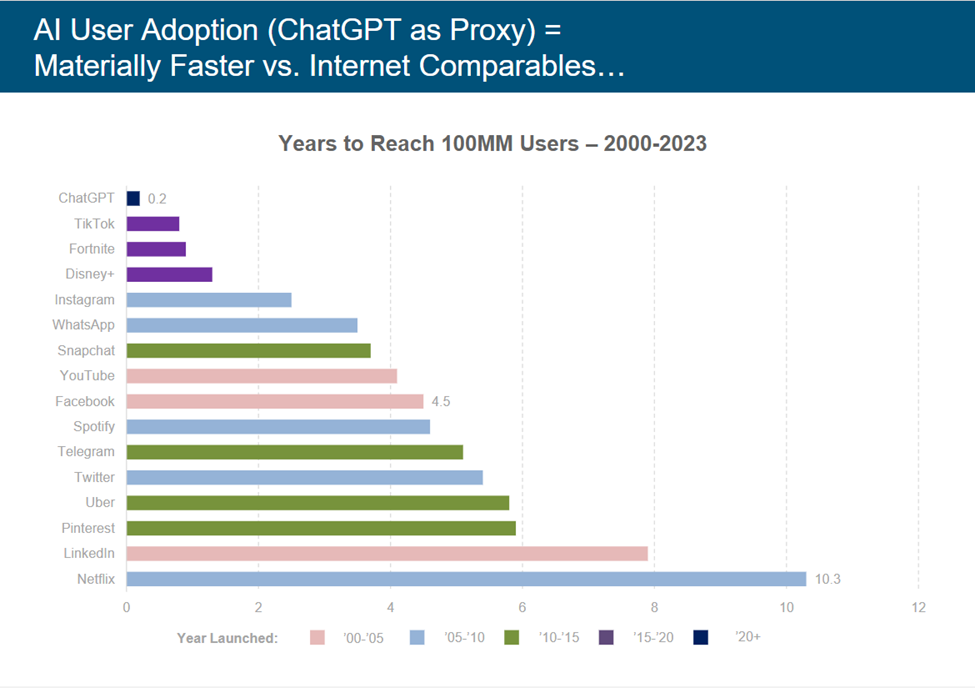
Now, as we say in psychology, sit with this from the same deck: time (in years) to reach 100 million users, by platform.
The AI is coming to your company regardless of whether you're adopting it or not. You do not have an option to opt out.
And that means that your cybersecurity process is now a target of 'bad actors' using AI.
We'll build this out later but there are things you're doing with your company's AI that is making you a target of bad actor AI. In a nutshell, the more you use agents as part of your AI platform the more inviting those agents become as bad-actor AI targets.
In one ironic way this is good for your cybersecurity process. In days of AI yore...like, last year...you didn't really need to know how your company's cybersecurity platform worked; you had CIOs or CISOs or CTOs who told you it worked. Because AI is transforming 'bad actor' options so quickly, now you need to re-build your cybersecurity strategy.
As part of the cybersecurity re-build that you must undertake, CIOs (etc.) need to collaborate more closely with other senior managers to clarify what is being done to prepare the organization both to leverage AI and build defensive models. That collaboration and clarification is what we mean by white box cybersecurity.
A black box, to quote directly from Wikipedia, "is a system which can be viewed in terms of its inputs and outputs (or transfer characteristics), without any knowledge of its internal workings. Its implementation is 'opaque' (black)." In the realm of AI, the function of deep learning can be thought of as a black box: the system trains itself for reasons that are not clear.
In contrast a white box is a system whose processes are known. That's what makes it your ally. As an executive or board member, you are now responsible for working with your technical leaders to create a cybersecurity risk management strategy. It needs to be trained appropriately to manage attacks by black-box systems. It needs to be transparent so that you can control it. It needs to be scalable so that you can grow it.
It needs to be a white box cybersecurity system.
Ask us how we can work with you to develop a white-box cybersecurity system that is simple, real, and effective. You cannot put this off.


Comments
Post a Comment